Role-Based Access: How to Delegate Without Losing Control
Learn how to set up role-based access (RBAC) and activity logs for property management. Includes a ready-to-use role matrix, least-privilege & separation-of-duties tips, and an audit-log checklist aligned to NIST/ISO/OWASP.
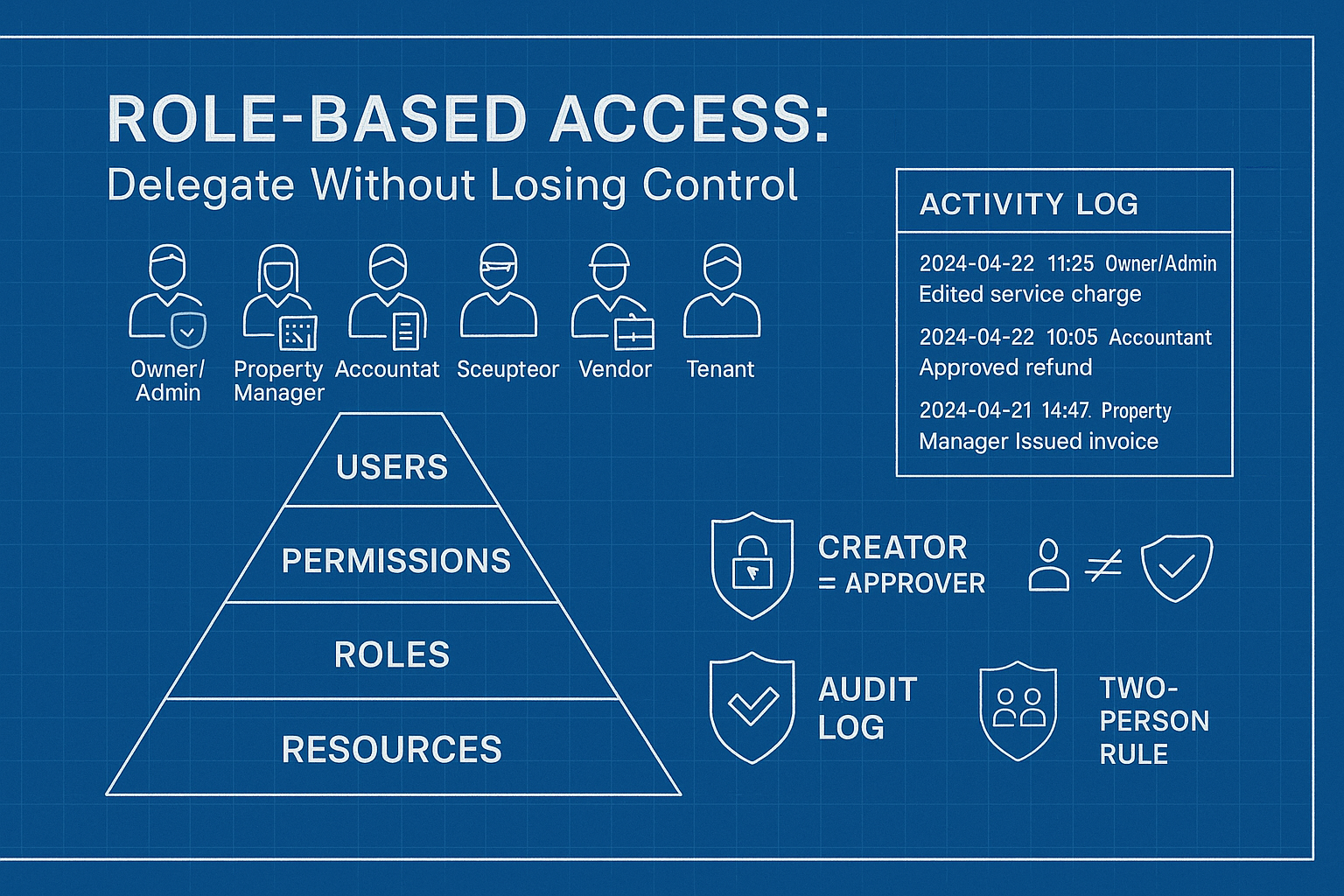
TL;DR
Use RBAC (roles → permissions → resources) to give each teammate only what they need (least privilege) and split high-risk duties (separation of duties). Pair this with tamper-resistant activity logs so every sensitive action (payments, lease edits, role changes) is traceable. This approach mirrors industry standards (NIST RBAC, NIST SP 800-53 AC-5/AC-6, AU-2/AU-6; ISO 27001 logging; OWASP ASVS). OWASP Cheat Sheet Series+7NIST Computer Security Resource Center+7The ANSI Blog+7
What RBAC actually is (plain English)
- Users are assigned to roles (e.g., Accountant, Site Supervisor).
- Roles carry permissions (e.g., “approve refunds”, “edit service-charge rates”).
- Permissions apply to objects/resources (buildings, units, invoices, tickets).
This is the classic model first standardized as ANSI/INCITS 359 (NIST RBAC). NIST Computer Security Resource Center+1
Two security principles you must enforce
- Least privilege: give only the access needed to do the job (NIST AC-6). CSF Tools
- Separation of duties: split risky steps so no single person can abuse power (NIST AC-5). CSF Tools
SoD examples:
- The person who creates a refund cannot approve it.
- The person who invites a vendor cannot approve vendor payouts.
- Two-person approval for rate changes and high-value refunds (dual control).
(These map directly to NIST AC-5/AC-6 expectations.) CSF Tools+1
Activity-log playbook (audit-ready)
What to log (minimum set aligned to standards):
- Auth & session: logins, MFA attempts, failures, device/IP. (NIST SP 800-92) NIST Publications
- Access control changes: role/permission grants, revokes, and elevation requests (who → what → when). (NIST SP 800-53 AU-2) CSF Tools
- Financial events: invoice issued, payment posted, refund request/approval, late-fee changes.
- Sensitive data: export/download of PII, owner statements, ledger exports. (OWASP logging guidance) OWASP Cheat Sheet Series
- Records & config: service-charge rate edits, lease amendments, vendor bank changes.
- System actions: failed jobs, API errors, webhook retries.
Quality rules:
- Use structured logs (JSON fields: actor_id, role, object_id, action, outcome, ip, user_agent, trace_id).
- Tamper-resistance: append-only store or WORM/S3 Object Lock + hash chain.
- Review cadence: daily for financial/admin actions; weekly summary to owners (NIST AU-6). CSF Tools
Retention hints: Keep operational logs hot for 90–180 days, archive for 1–7 years with encryption + access controls (aligns with ISO 27001 logging objectives; confirm with your auditor/regulations). ISMS.online
Implementation guide (property teams)
- Define scopes first
Break permissions by resource + action (e.g.,building:read,invoice:approve,rate:edit). Map them to roles; avoid “God mode” roles. - Use RBAC + ABAC (hybrid)
RBAC sets the baseline; add attributes to narrow access (e.g., Manager can edit only assigned buildings; Accountant can view only finance). This matches OWASP ASVS access-control verification goals. OWASP+1 - Enforce SoD in workflows
Configure two-person approvals for refunds, write-offs, and service-charge changes. Block “creator approves own item.” - Least-privilege lifecycle
- Joiners: start with minimal role; escalate via ticket/approval.
- Movers: time-box elevated roles (auto-revert in 7/30 days).
- Leavers: immediate disable + forced session revocation (covers AC-2 account lifecycle). NIST Publications
- Instrument audit trails
Ship structured logs to a centralized sink (e.g., ELK/OpenSearch/SIEM). Configure alerts for: new admin grants, export downloads, rate changes, and repeated failed logins (OWASP + NIST guidance). OWASP Cheat Sheet Series+1 - Prove it (reviews & reports)
- Quarterly access review (role → user list; exceptions corrected).
- Monthly AU-6 review: summarize suspicious events; tie to incident response. CSF Tools
Example: practical policy clauses
Least Privilege (Admin handbook)
“Access is provisioned by role and minimized to job need. Elevated roles are time-boxed and require ticket-based approval. Self-approval of refunds, payouts, or rate changes is prohibited.” (Aligns with NIST AC-6, AC-5.) CSF Tools+1
Audit Logging (SaaS config)
“The system records authentication, permission changes, financial events, data exports, and configuration edits with actor identity, timestamp, and object identifiers. Logs are immutable and reviewed under AU-6.” CSF Tools+1
KPIs & alerts to track
- Privileged accounts (target: < 3% of users).
- Dormant privileged users (target: 0).
- Admin-grant alerts resolved (≤ 24h).
- Export/download events (investigate spikes).
- Refunds self-approved (should be 0).
- Log coverage (% of critical actions producing events) (target: 100%).
These align with the spirit of OWASP ASVS and NIST AU controls. OWASP Cheat Sheet Series+1
Common mistakes (and fixes)
- “One super-admin for everything.” → Split admin into Tenant Admin, Finance Admin, Ops Admin.
- Static access forever. → Time-boxed elevations with auto-revert.
- Logs without context. → Use structured fields + correlation IDs.
- No review process. → Schedule monthly AU-6 reviews; send owner summary. CSF Tools
FAQ
Q: Isn’t RBAC too rigid for growing teams?
Use RBAC for clarity, then add ABAC conditions (building assignment, region, shift) for flexibility—an approach consistent with modern access-control verification guidance (OWASP ASVS). OWASP
Q: What exactly should I review each month?
New admin grants, role changes, failed logins, data exports, refund/waiver approvals, and any edits to service-charge rates or bank details (NIST AU-2/AU-6 themes). CSF Tools+1
Q: How long should we keep logs?
Keep hot for 90–180 days and archive for 1–7 years depending on finance/audit needs and local regulation; protect integrity per ISO 27001 logging guidance. ISMS.online
How this looks in your software
- Roles: Owner/Admin, Property Manager, Accountant, Site Supervisor, Vendor, Tenant.
- Guards: Dual-approval for refunds; creator ≠ approver; edits to rates require two people.
- Logs: Immutable, structured; exportable for auditors; alerts on admin grants & data exports.
Sources
- NIST RBAC model & ANSI/INCITS 359 standard. NIST Computer Security Resource Center+1
- NIST SP 800-53 Rev.5 controls (AC-5, AC-6; AU-2, AU-6) and database/derivative docs. CSF Tools+5NIST Publications+5NIST Computer Security Resource Center+5
- NIST SP 800-92 Guide to Computer Security Log Management. NIST Publications+1
- OWASP ASVS & Logging Cheat Sheet (access-control verification & logging best practices). OWASP+2OWASP Cheat Sheet Series+2
- ISO/IEC 27001:2022 Annex A 8.15 Logging overviews. ISMS.online+1
Expert insights from the Property Studio team on property management, real estate, and digital solutions.
